SECURITY
Our Mission @ Halodoc
Halodoc is a secure health-tech platform with a mission to simplify access to healthcare by connecting millions of patients with licensed doctors, insurance, labs, and pharmacies through simple mobile applications.Program Rules
If you are working on this program, you must abide by all of these following rules:- You must be the first reporter of a valid vulnerability, known vulnerabilities or submissions by researchers leading back to the same root cause will be classified as a duplicate finding.
- You are not authorised to access user data or company data, including (but not limited to) personally identifiable information and data relating to an identified or identifiable natural person, except as part of vulnerability validation.
- All automated scanning must include “<your name>/security_researcher” in the user agent in order to be eligible for reward.
- Denial of service attacks are prohibited.
- Public or private disclosure of a vulnerability is prohibited.
- Never attempt non-technical attacks including, but not limited to, social engineering, phishing or physical attacks.
- You are not a current or former employee of Halodoc.
- In the event of non-compliance with the rules stated herein, Halodoc reserves the right to take legal action or initiate a law suit against you.
How to report the issues discovered?
If you discover potential security vulnerabilities in any application or asset that comes within the scope of the program, please use this Google Form for submission(s).SLA for triaging of issues according to the severity
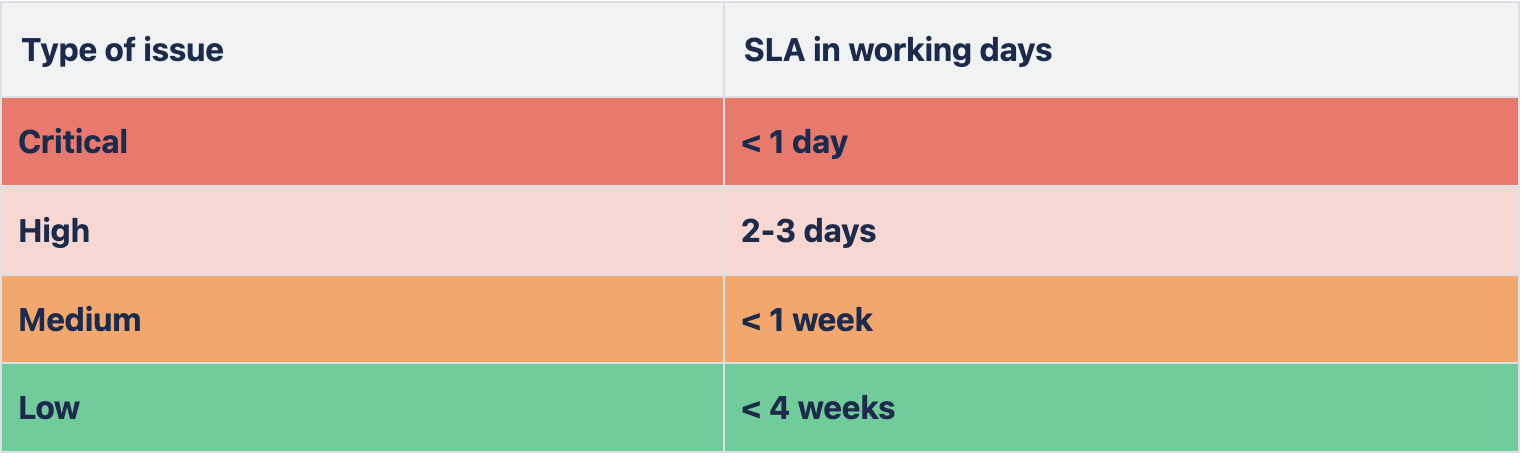
Bug Bounty Scope and Rewards
Halodoc will only reward the first reporter of a vulnerability and only if it is deemed to be in scope and reported in compliance with this policy.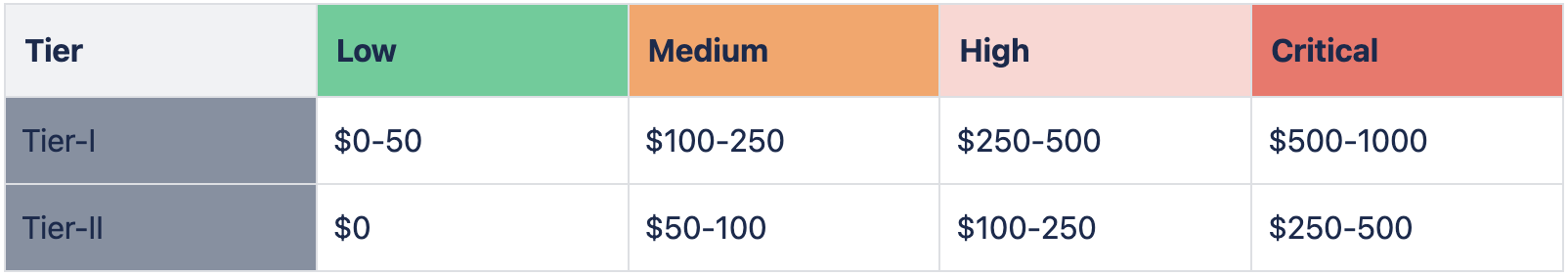
Tier-I Assets
- Halodoc Android Applications:
- Halodoc iOS Applications:
- *.halodoc.com
Tier-II Assets
- *.stage.halodoc.com or any other staging environment*All staging environment that are not reproducible in the Production environment will be eligible for Tier-II Rewards.
- blogs.halodoc.io
Do’s
High quality submissions allow our team to understand the issue better and engage the appropriate teams to fix. The best reports provide enough actionable information to verify and validate the issue without requiring any follow up questions for more information or clarification.- Check the scope before you begin writing your report to ensure the issue you are reporting is in scope for the program.
- Think through the attack scenario and exploitability of the vulnerability and provide as many clear details as possible for our team to reproduce the issue (include screenshots/Video PoC when applicable).
- Please include your understanding of the security impact of the issue. Our bounty payouts are directly tied to security impact, so the more detail you can provide, the better. We cannot payout after the fact if we do not have evidence and a mutual understanding of security severity.
- In some cases, it may not be possible to have all of the context on the impact of a bug. If you are unsure of the direct impact, but feel you may have found something interesting, feel free to submit a detailed report and ask.
Dont’s
- Do not leave any system in a more vulnerable state than you found it.
- Do not use or interact with accounts you do not own.
- Do not brute force credentials or guess credentials to gain access to systems or accounts.
- Do not change passwords of any account that is not yours or that you do not have explicit permission to change. If ever prompted to change a password of an account you did not register yourself or an account that was not provided to you, stop and report the finding immediately.
- Do not perform denial of service (DoS) attacks or related tests that would cause availability interruptions or degradation of our services.
- Do not disclose a vulnerability submission, as our bug bounty program prohibits both public and private disclosures.
- Do not engage in any form of social engineering of Halodoc employees, customers, or partners.
- Do not engage or target any specific Halodoc employees, customers, or partners during your testing.
- Do not access, extract, or download personal or business information beyond that which is minimally necessary for your Proof-of-Concept purposes.
- Do not do anything that would cause destruction of Halodoc data or systems.
- Respect user privacy and confidentiality, refrain from accessing or tampering with sensitive data.
- Comply with all applicable laws and regulations during the research process.
Out-Of-Scope
- Web applications and APIs
- HTTP 404 codes/pages or other HTTP non-200 codes/pages.
- Fingerprinting/banner disclosure on common/public services.
- Disclosure of known public files or directories (e.g., robots.txt).
- Getting OTPs is expected behaviour for countries other than Indonesia.
- Issues that require non-simple user interaction, such as Self-XSS, clickjacking, that require the victim to install a certain application and interact with it, and issues that require MITM or access to physical devices.
- Clickjacking on pages with no sensitive actions.
- CSRF on forms that are available to anonymous users (e.g., login or contact form).
- Logout / Login Cross-Site Request Forgery (logout CSRF).
- Presence of application or web browser ‘autocomplete' or ‘save password' functionality.
- Lack of Security Speed Bump when leaving the site.
- No Captcha / Weak Captcha / Captcha Bypass.
- Login or Forgot Password page brute force and account lockout not enforced.
- HTTP method enabled OPTIONS, PUT,GET,DELETE,INFO.
- WebServer Type disclosures.
- Social engineering of our service desk, employees, or contractors.
- Physical attacks against Halodoc's offices and data centers.
- Error messages with non-sensitive data.
- Non-application layer Denial of Service or DDoS.
- Lack of HTTP Only / SECURE flag for cookies.
- Username / email enumeration: via Login Page error message | via Forgot Password error message.
- Missing HTTP security headers.
- CSV Issues.
- AV Scanning.
- SSL Issues.
- Cookie Issues:
- HTTPONLY
- SECURE
- Multiple cookie setting
- Anything to do with JSESSIONID
- Service Rate Limiting.
- User or Org enumeration.
- Security Image Issues.
- For Mobile Applications
- No or ineffective jailbreak / root detection.
- No or ineffective anti-reversing controls (e.g. obfuscation, runtime tampering, debugging, emulator detection).
- No or ineffective certificate validation and pinning.
- Disclosure of paths in binary (such as file system paths of the system where the app was compiled).
- Disclosure of API keys for non-sensitive uses.
- Exploits only possible upon a jailbroken or rooted end user device.
Our Promises
In return for your dedication to improving our security posture, we commit to:- Promptly acknowledging receipt of your report.
- Thoroughly assessing and validating the reported vulnerabilities.
- Keeping you informed about the progress and resolution of the reported issues.
- Offering fair and timely rewards for eligible submissions.
Hall of Fame
2025
- Rahmadhani Novian Jaya
- Ade Yosep Yarmanto
- Faisal Yudo Hernawan
2024
- Lu William Hanugra ||
LinkedIn - Alexander Christian ||
LinkedIn - Alvin Ferdiansyah ||
LinkedIn - M. Alfan Nur Hanif ||
LinkedIn - Wael Ahmed ||
LinkedIn - Firza Insanudzaky ||
LinkedIn - Muhammad Sayuti ||
LinkedIn - Azhari Harahap ||
LinkedIn
2023
- Parlan
- Zukhrufan Ramadhan
2022
- Haerudin
- passthebug1337@gmail.com
2021
- Abdullah
- Erlin Silistyani St
- Erlin Sulistyani x2
- Haerudin
- Mohamad Arifandy
- Pratama Aji Prisadi
2020
- Abdullah x2
- Ade Yosep Yarmanto
- Adith Yogaswara
- Amurul Islam x2
- Ari Rosmiyati
- Emanual Beni
- Erlin Sulistyani
- Irwan
- M Arif Alfiki
- M Wahyudi
- Rendra Wahyu Febriyanto
- Rizky Sulistyo
- Root Bakar
- Yogeshwaran Chandrasekaran x2
- Yulianti Rahayu
2019
- Abdullah
- Aldi Saputra Wahyudi x2
- Alfons x2
- Arya Tunggal Narotama
- Faisal Yuda Hermawan
- Ibnu Batutah Zarizal x3
- Lu William Hanugra
- Muhammad Adib Arinanda
- Turab Ameer x2
- Yogeshwaran Chandrasekaran x2
- Zulfikar Adnan
2018
- Debby Nawang Sari
- Kusum Lata
- Rahul
- Roholesi Talaohy
- Sudaryati